
Towards Large-Scale, Heterogeneous Anomaly Detection Systems in Industrial Networks: A Survey of Current Trends
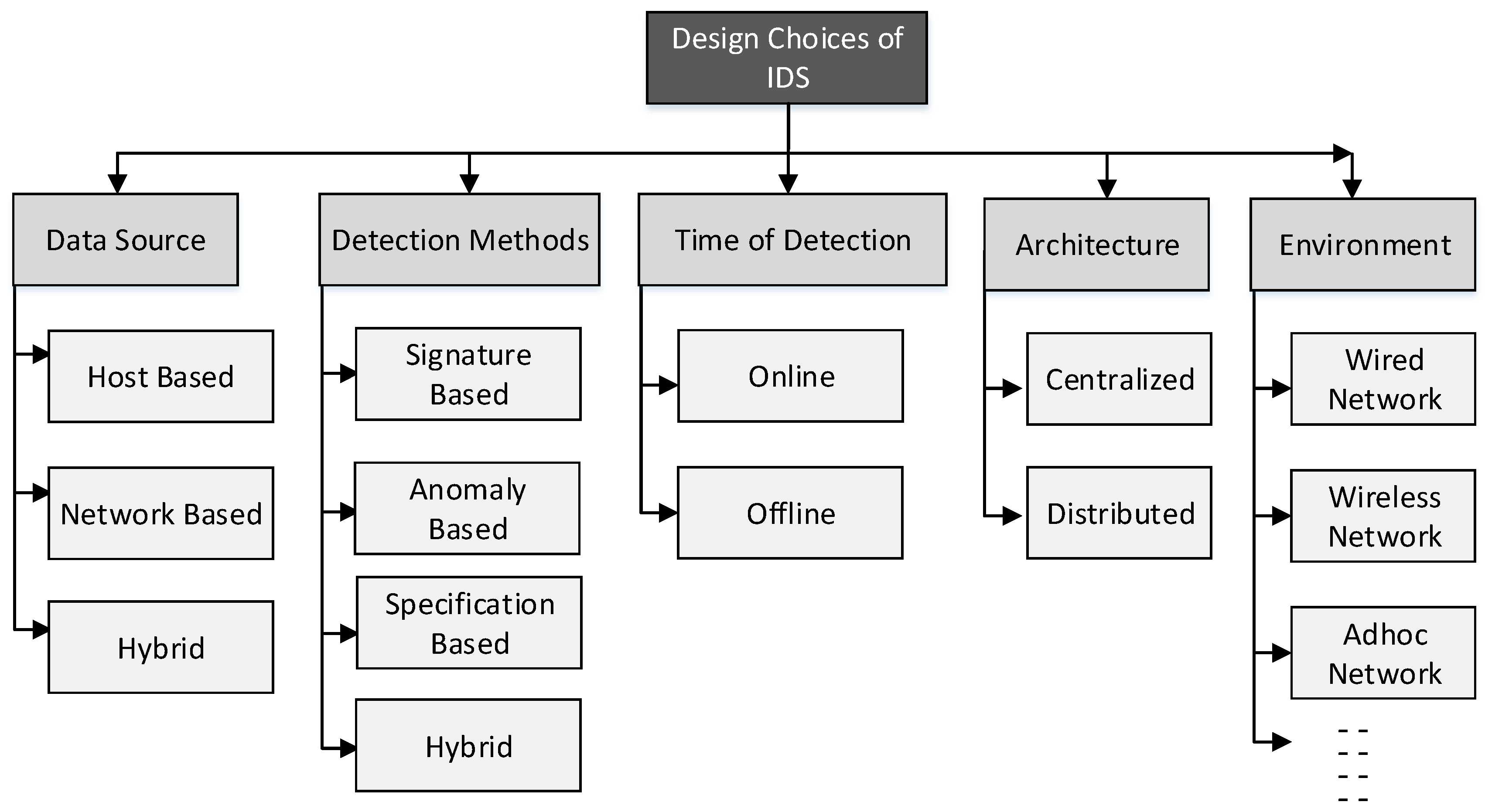
Electronics | Free Full-Text | A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions | HTML

Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

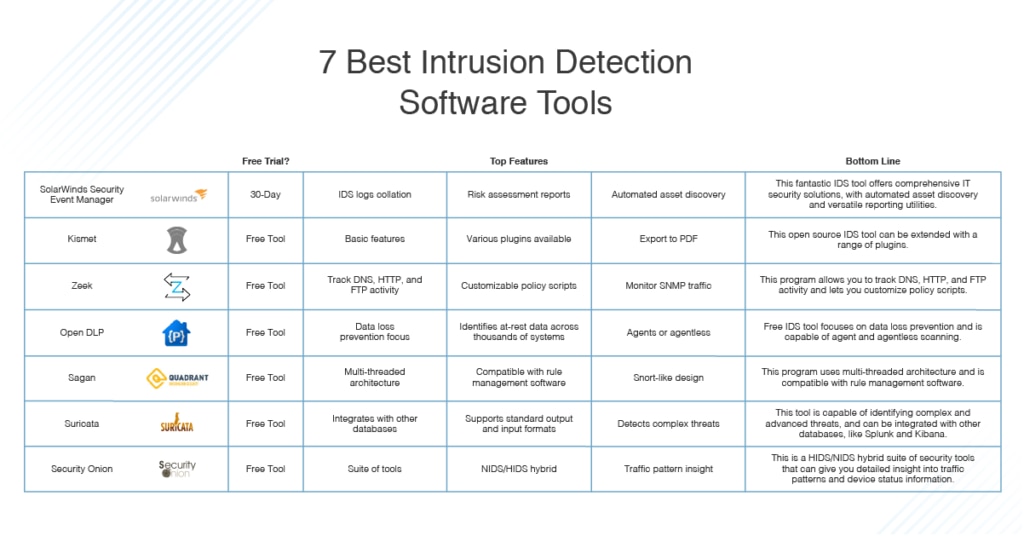

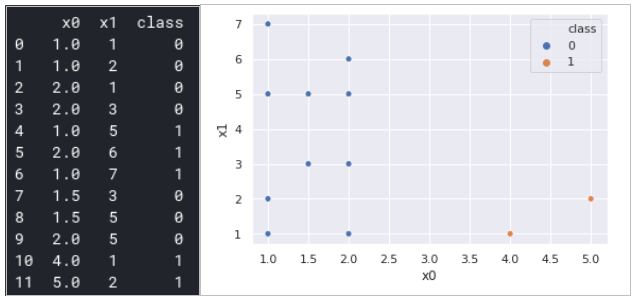

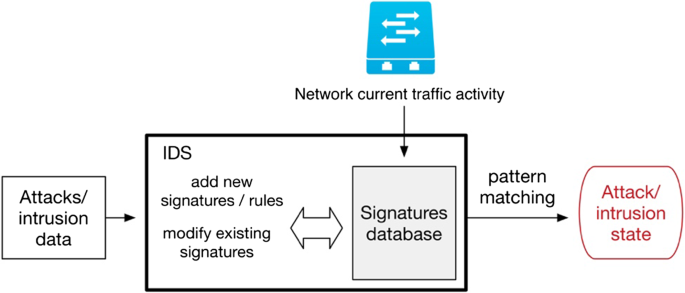

![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/20-Figure13-1.png)
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/12-Figure8-1.png)
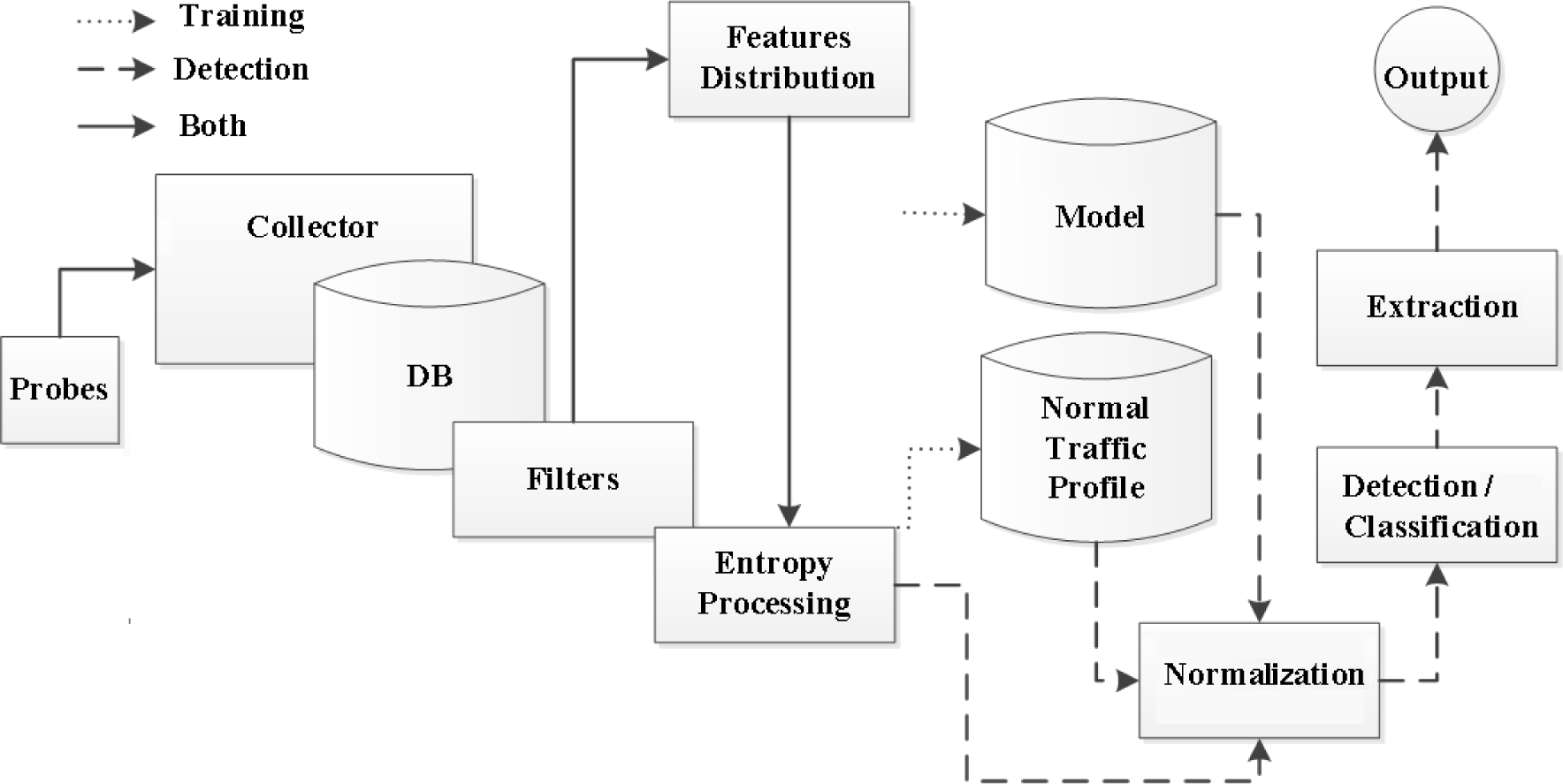
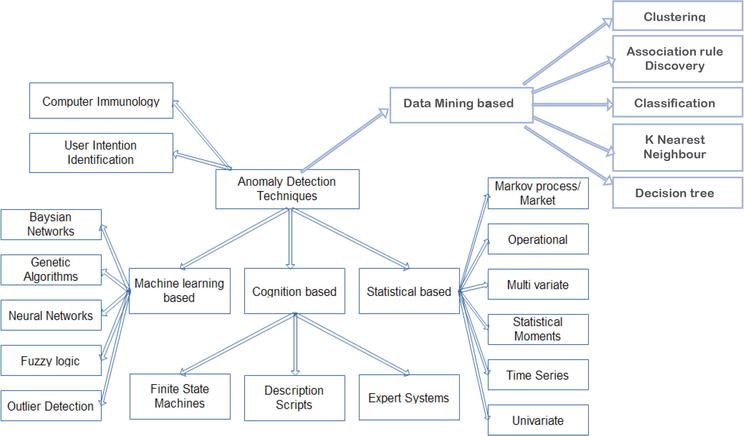

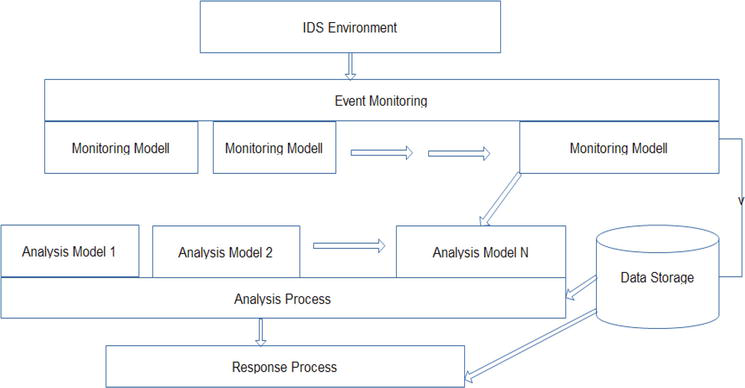

![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/16-Figure11-1.png)
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/5-Figure1-1.png)



![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/18-Figure12-1.png)