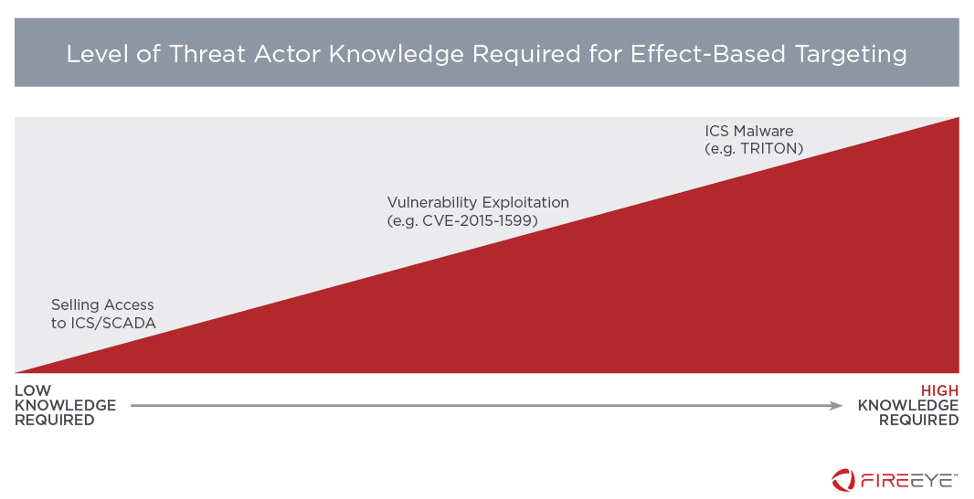
Monitoring ICS Cyber Operation Tools and Software Exploit Modules To Anticipate Future Threats | Mandiant
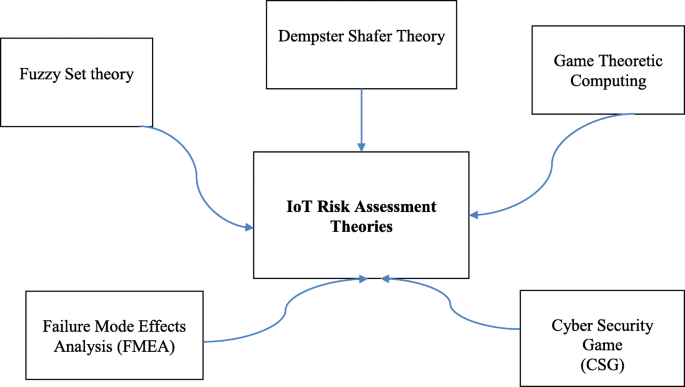
IoT cyber risk: a holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process | EURASIP Journal on Information Security | Full Text

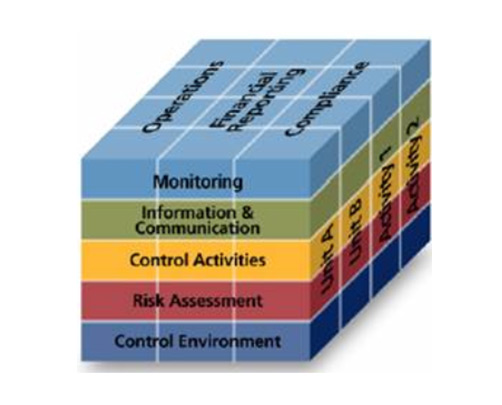
Table 2.1 from A Model Assessment Tool for the Incident Command System: A Case Study of the San Antonio Fire Department | Semantic Scholar
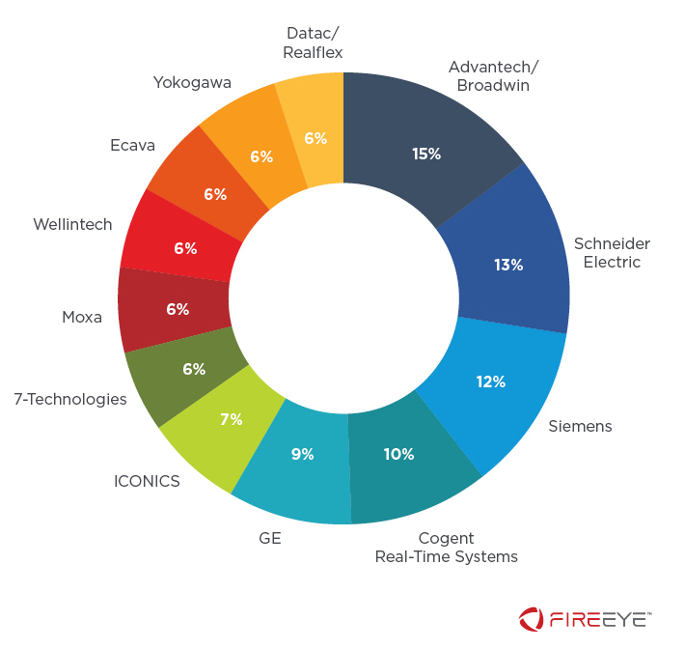
Monitoring ICS Cyber Operation Tools and Software Exploit Modules To Anticipate Future Threats | Mandiant
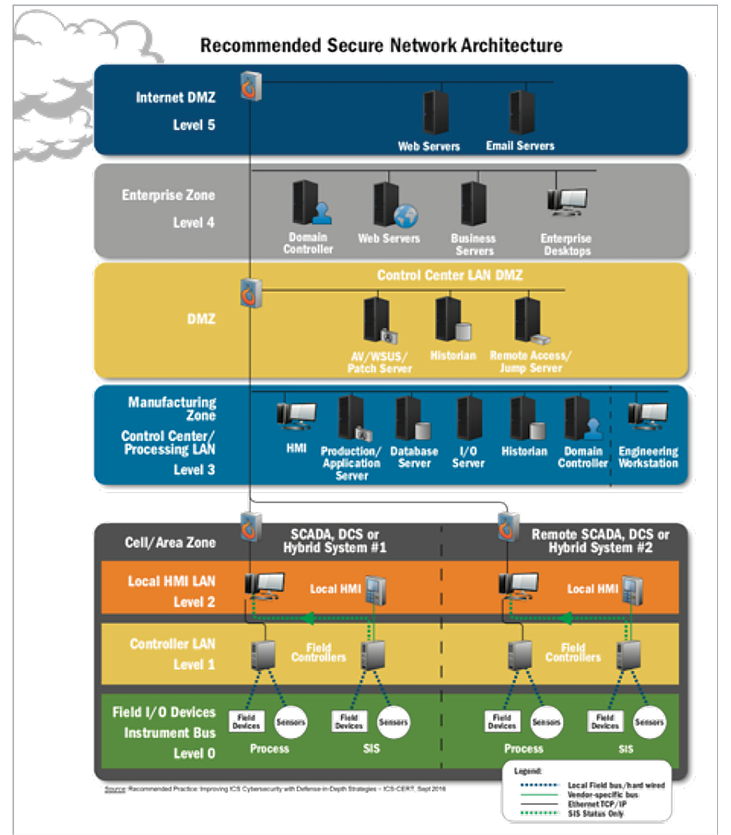
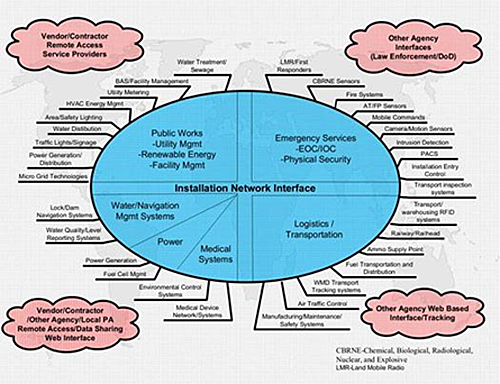
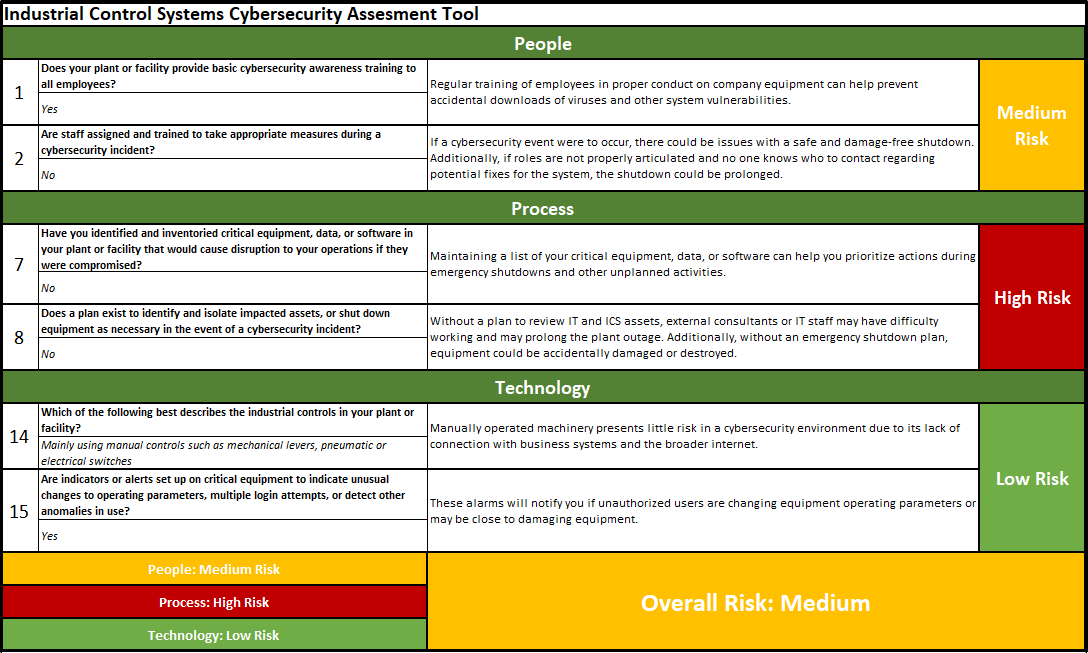
Practical Industrial Control System (ICS) Cybersecurity: IT and OT Have Converged – Discover and Defend Your Assets - CSIAC