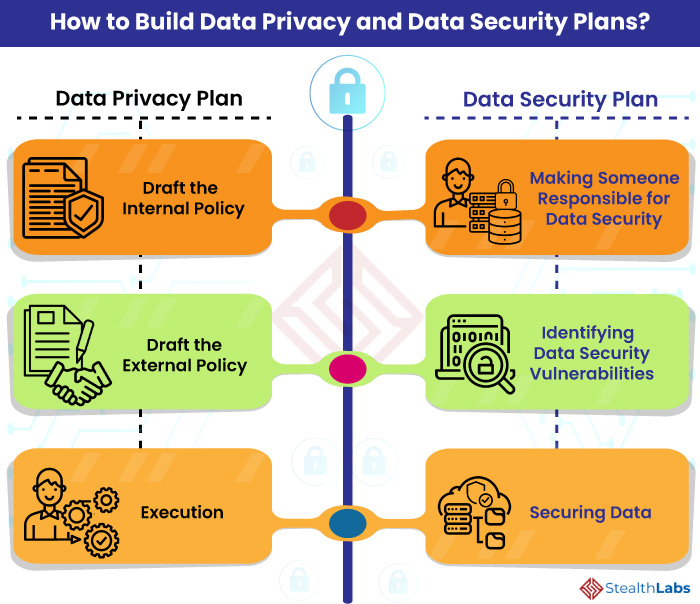
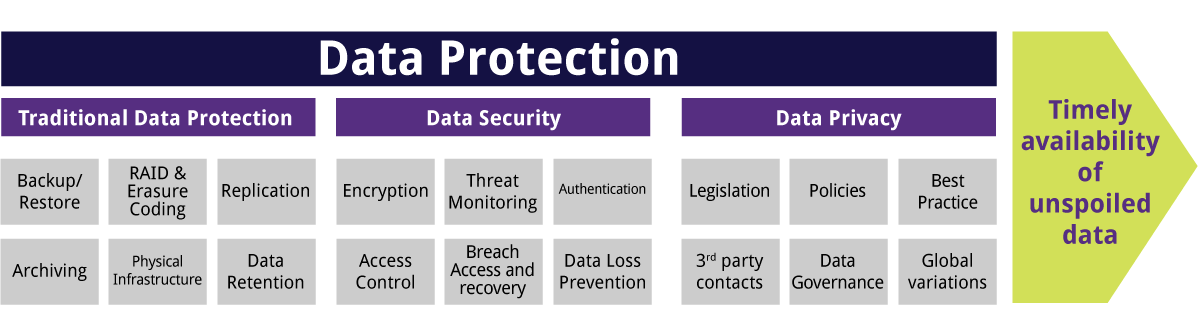
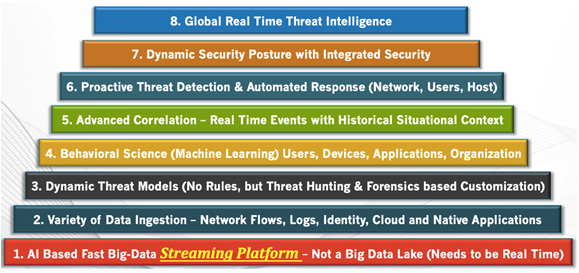
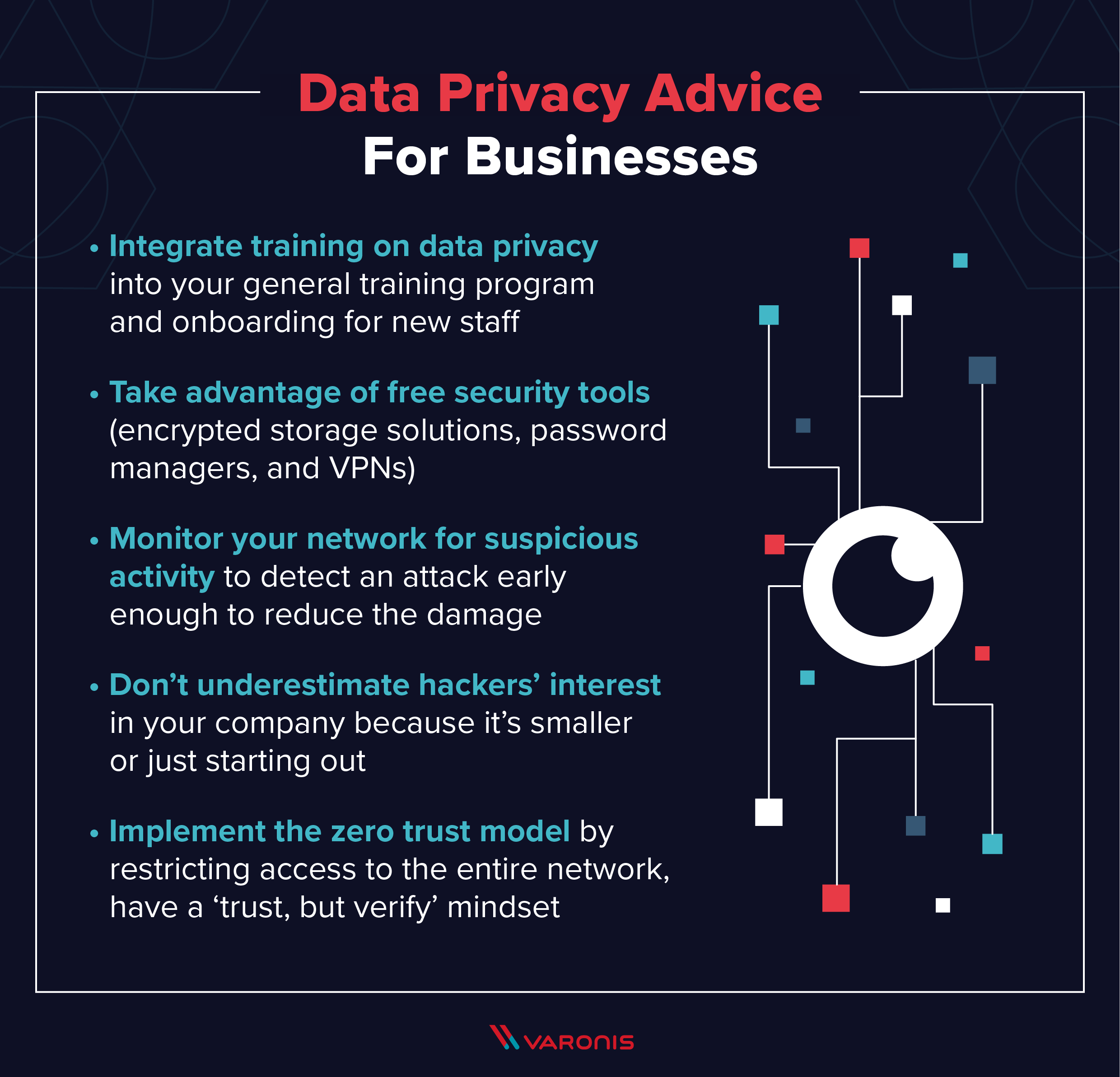
Official PCI Security Standards Council Site - Verify PCI Compliance, Download Data Security and Credit Card Security Standards

Devoteam on Twitter: "Data #protection and #security is key to every business. Know the best #practices to secure your #information network and #people. Find what could be improved in your company by

Professor Kevin Curran – Page 14 – Technology Communicator, Researcher & Professor at Ulster University
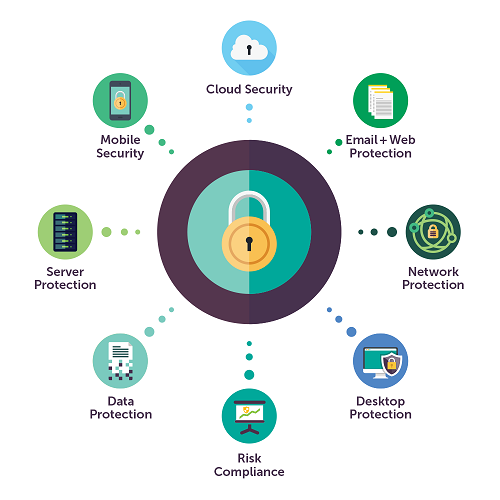
Enterprise Endpoint Security – Rules to Protect from Advanced Malware and Security Breaches – Xorlogics