Privacy and Data Security Worldwide: 2020 and Beyond | Kramer Levin Naftalis & Frankel LLP - JDSupra

Cyber Security Law Digital Legislation 3d Illustration Shows Digital Safeguard Legislation To Protect Data Privacy Stock Photo - Alamy
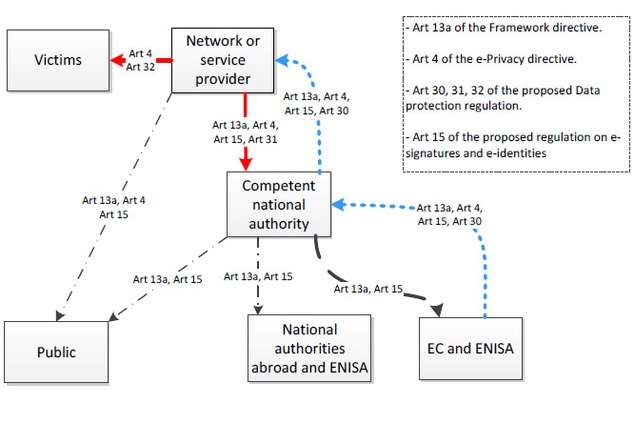
EU agency ENISA analyses cyber security legislation & spots implementation gaps; incidents remain undetected or not reported — ENISA










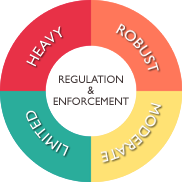

![Tech Law] China's Big Data Era. New law for Data Protection | HFG Tech Law] China's Big Data Era. New law for Data Protection | HFG](https://www.hfgip.com/sites/default/files/media/Images/articles_21/data_protection_table.png)